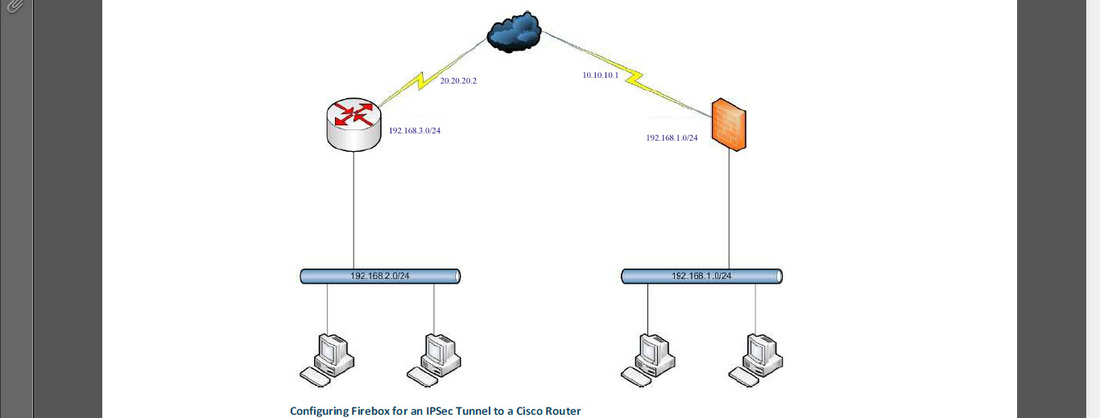
Video : How to configure Watchguatd and cisco router IPSEC secured VPN
Step by Step procedure how to configure Watchguatd and cisco router IPSEC secured VPN
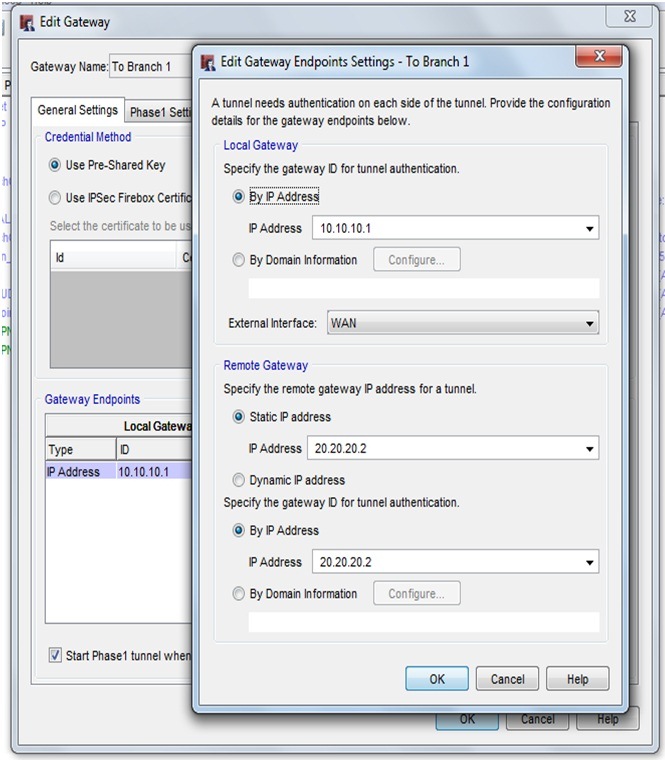
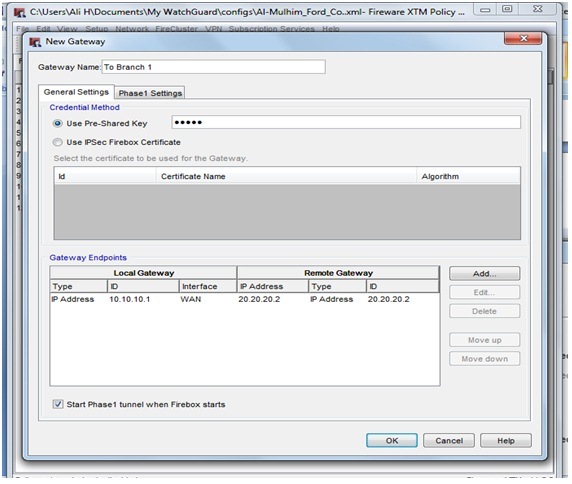
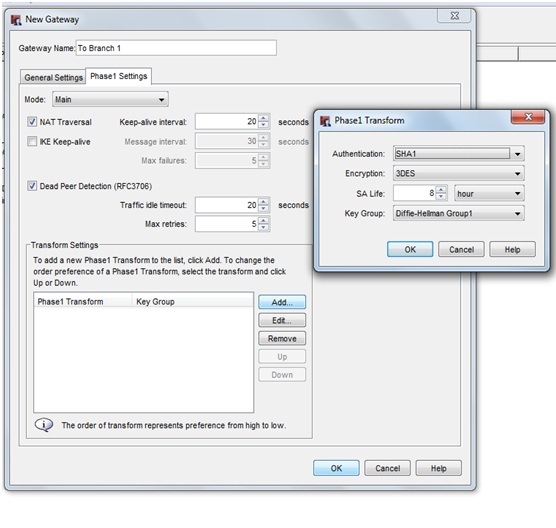
In watchguard Policy manager goto VPN>Branch Office Gateways>Add
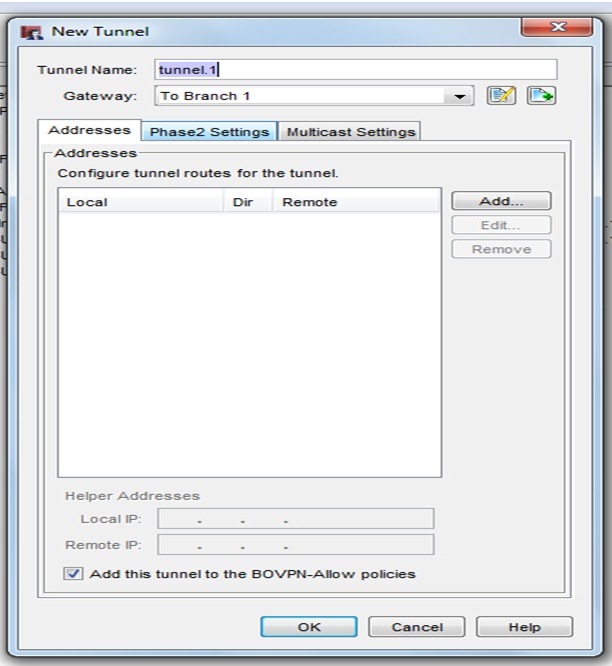
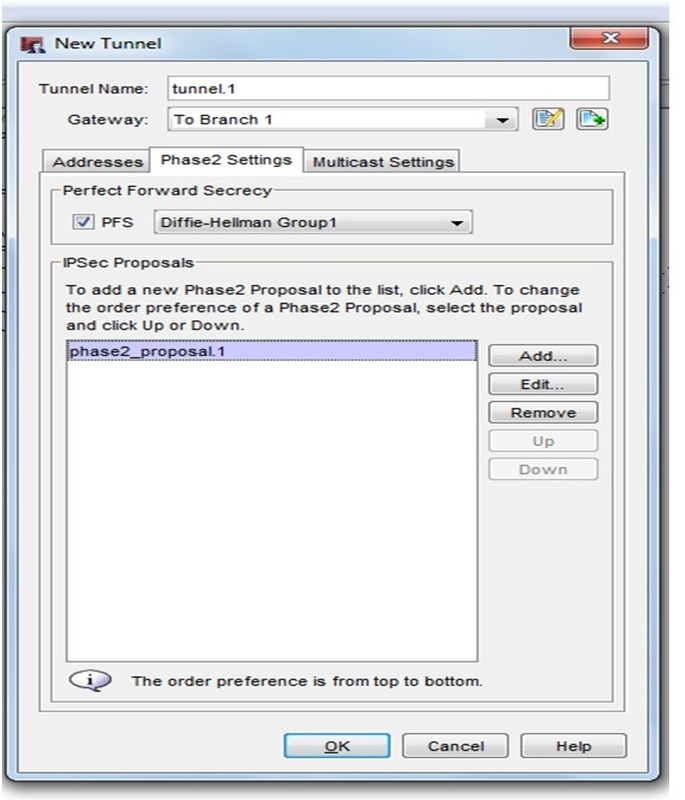
After creating gateway Goto VPN> Branch Office Tunnels
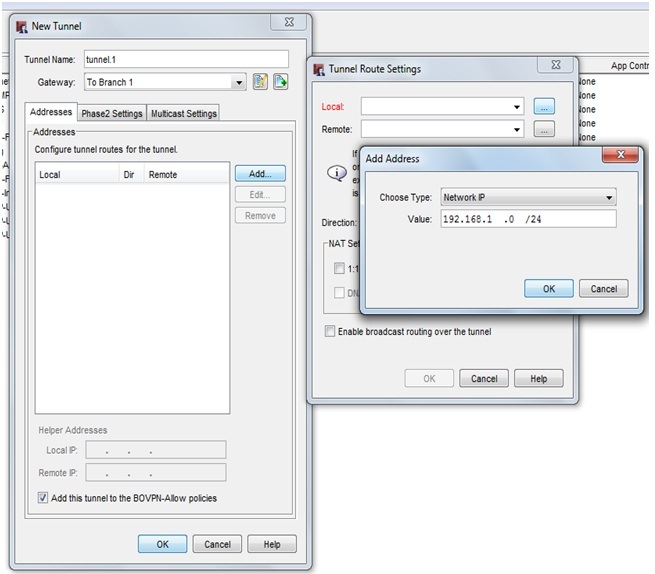
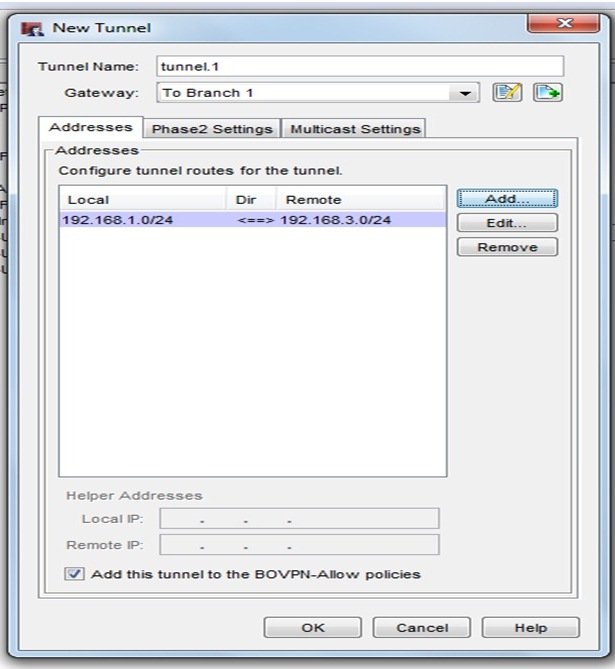
Select the same gateway which you created before . GOTO address >ADD (add the local subnet and remote subnet)
Select the same gateway which you created before . GOTO address >ADD (add the local subnet and remote subnet)